Table of contents:
|
1. What Is Cybersecurity Risk & Why Frameworks Matter |
|
2. NIST Cybersecurity Framework (CSF 2.0) |
|
3. ISO/IEC 27001 & ISO/IEC 27002 |
|
4. CIS Critical Security Controls |
|
5. SOC 2 |
|
6. COBIT & Governance-Oriented Frameworks |
|
7. Others to Watch: PCI DSS, HIPAA, Zero Trust, CTEM, etc. |
|
8. How I Teach Integration & Realization |
|
9. Final Thoughts |
|
10. Frequently Asked Questions (FAQs) |
Cybersecurity Frameworks are not just trendy terms. They are important guides we use at Apponix. These frameworks help organisations develop, evaluate, and enhance their defense strategies.
In this blog, I will guide you through important security frameworks. I will explain what cybersecurity risk is and how to manage it. I will also show you how these frameworks relate to real-world needs.
By the end, you will see which frameworks are most important today. You will also learn how a Cyber Security course in Bangalore, like ours, can help you use them.
What Is Cybersecurity Risk & Why Frameworks Matter
Before diving into frameworks, let’s clarify what is cybersecurity risk. In simple terms, cybersecurity risk is the chance of losing, damaging, or disrupting your digital assets. These assets include data, systems, and services.
This risk arises from threats that exploit vulnerabilities. Organizations face risks from phishing, ransomware, supply chain attacks, and insider threats.
When we talk about managing cybersecurity risk, we mean identifying risks, prioritizing them, applying controls, monitoring, and iterating. This is where security frameworks come in.
These cybersecurity standards or security frameworks are like guides. They provide best practices, processes, and controls to lower risk. Different frameworks types exist depending on industry, maturity, compliance, and scale.
In 2025, a few frameworks stand out, and I always include them in my classes at Apponix.
NIST Cybersecurity Framework (CSF 2.0)
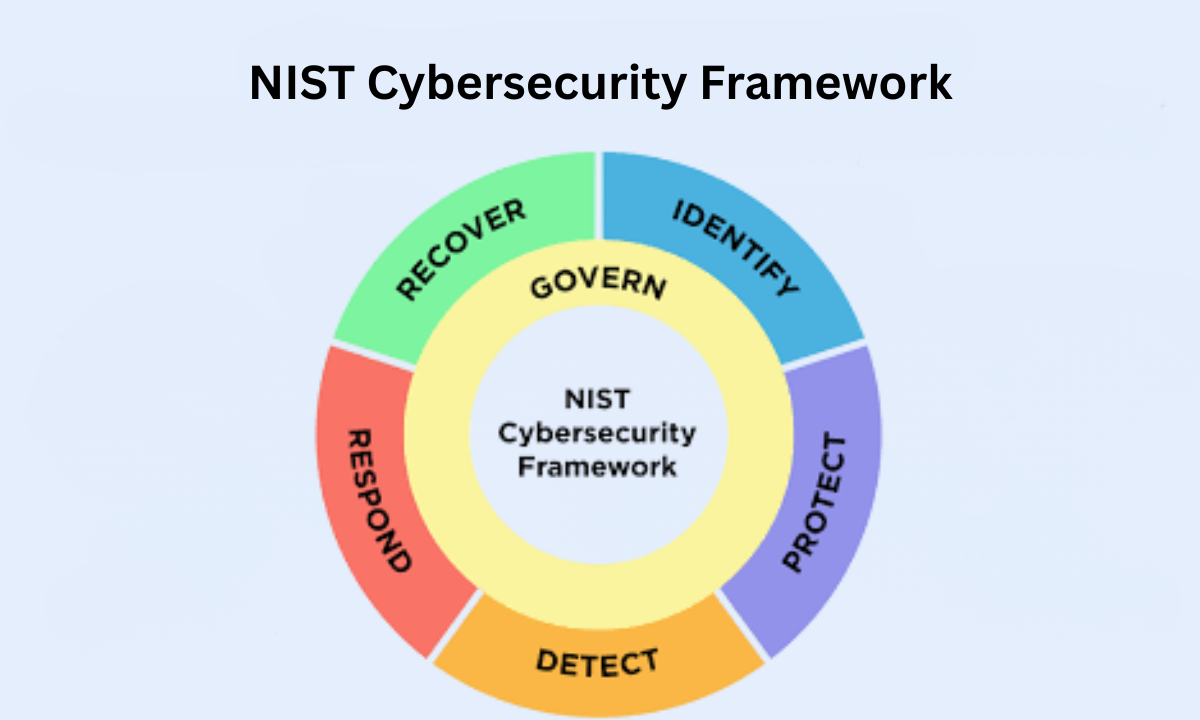
This remains the gold standard. The NIST cybersecurity framework, now called CSF 2.0, has six main functions: Govern, Identify, Protect, Detect, Respond, and Recover.
What makes it powerful is flexibility—you pick what’s relevant and scale gradually. Many organizations start with “Identify” and “Protect,” then evolve toward full maturity. It also maps well to enterprise risk management.
As a trainer, I focus on how we map existing controls. These controls come from ISO, CIS, or our own policies. We do this to fit them into the NIST framework. This helps ensure clarity and consistency.
ISO/IEC 27001 & ISO/IEC 27002
ISO 27001 is an international standard to build an Information Security Management System (ISMS). ISO 27002 gives you a catalog of controls and guidance on applying them.
NIST is a flexible framework that is mostly voluntary. In contrast, ISO 27001 offers formal certification. This certification helps with compliance, builds vendor trust, and boosts client confidence. But certifications are point-in-time; continuous monitoring is essential to keep pace with evolving threats.
In our Cyber Security course in Bangalore, I make sure learners know how to read ISO controls. I also teach them how to combine these with NIST for better results.
CIS Critical Security Controls
The CIS Controls (now evolving) are essentially a prioritized set of defensive actions—“start here, then move up.” They are tactical and highly practical.
These controls help bridge theory and action. In training, we use them for labs: e.g. patching, least privilege, logging, and incident detection workflows. Because you can implement them in small increments, they’re ideal for organizations just getting serious about cybersecurity.
SOC 2
SOC 2 is not a controls framework. It is an audit standard used mainly for service organizations. This includes SaaS, cloud, and third-party vendors. Five Trust Services Criteria govern it: security, availability, processing integrity, confidentiality, and privacy.
Many Indian tech services and product firms seek SOC 2. This is because SOC 2 is common in the U.S. They want to meet the needs of international clients. In our training, I cover how to prepare for a SOC 2 audit as part of your governance and compliance roadmap.
COBIT & Governance-Oriented Frameworks
COBIT, created by ISACA, focuses more on governance and risk. It also looks at how IT aligns with business strategy.
I teach COBIT as a helpful addition. When organizations have controls from NIST or ISO, COBIT helps align those controls with their goals and stakeholders. It gives structure to decision-making.
Others to Watch: PCI DSS, HIPAA, Zero Trust, CTEM, etc.
Beyond the above, in 2025, you should be aware of:
-
PCI DSS: For organizations that handle credit card data, this remains a must-know standard.
-
Zero Trust models are not a standalone framework. However, many frameworks are now aligning with Zero Trust principles. These principles include identity, network segmentation, and least privilege.
-
Continuous Threat Exposure Management (CTEM): A newer paradigm emphasizing continuous scanning, exposure management, and dynamic controls.
-
We introduce learners at Apponix to CTEM as a modern mindset rather than a rigid checklist.
How I Teach Integration & Realization
As a trainer at Apponix, my approach isn’t “pick one and stick”—it’s about mapping and layering:
-
Start with risk assessment: Understand what matters (data, business, compliance) to your environment.
-
Map current controls: Maybe you already have logging, patching, access policies. Map them into frameworks like NIST or ISO.
-
Identify gaps and prioritize: Use CIS Controls for quick wins, or audit-level standards for deeper maturity.
-
Governance & alignment: Layer in COBIT or internal governance to ensure oversight.
-
Iterate: Use metrics, dashboards, audits, and reassess risk continuously.
In the Cyber Security course at Apponix in Bangalore, we have labs. In these labs, learners map real or mock infrastructure into different frameworks. They also perform gap analysis and create roadmap proposals. That hands-on alignment cements understanding.
Final Thoughts
We have explored important cybersecurity frameworks. These include the flexible NIST CSF 2.0 and the certified ISO 27001. We also looked at tactical CIS Controls and governance through COBIT. Additionally, we covered niche models like SOC 2, PCI DSS, and CTEM.
Understanding what is cybersecurity risk and managing cybersecurity risk is the foundation. Frameworks are tools to help you structure that journey.
If you want a career in cybersecurity, consider taking a Cyber Security course in Bangalore. Our course at Apponix has a strong curriculum that can help you get ahead. You’ll learn not only theory but also hands-on mapping of real systems into these frameworks. Over time, you’ll grow from trainee to practitioner—able to advise organizations on cybersecurity standards, adopt security frameworks, and continuously strengthen posture.
At Apponix Training Institute in Bangalore, I’m proud to help shape the next generation of security professionals. I’ve seen learners transition from knowing nothing about frameworks to designing security programs for firms. That’s the power of the right training combined with frameworks you can apply.
Frequently Asked Questions (FAQs)
Q1: Which cybersecurity framework should I learn first?
I usually recommend starting with NIST CSF 2.0—it provides a broad, adaptable foundation. From there, layer ISO, CIS, or governance frameworks depending on your interest or target industry.
Q2: How do I decide which framework is appropriate for an organization?
You consider the organization’s size, regulatory requirements, risk appetite, and existing maturity. A small startup may adopt CIS Controls first. A larger or regulated company may need ISO 27001 plus NIST plus governance frameworks.
Q3: Do organizations implement multiple frameworks at once?
Yes—that’s common. They map controls across frameworks to avoid duplication. For example, one control may satisfy a requirement in NIST and ISO simultaneously. That’s why I teach integration in our training.
Q4: How often should frameworks be reviewed or updated?
Continuously. The threat landscape evolves, so annual reviews, audits, and gap reassessments should be part of your process.
Q5: Will knowing these frameworks help me get a job in cybersecurity?
Absolutely. Many jobs need experience or knowledge of NIST, ISO, or SOC 2. Taking a Cyber Security course on these topics can help you in interviews. It will also prepare you for real-world challenges.